Authors Angèle Bossuat, Julio Loayza Meneses, Mihail Kirov, Sébastien Rolland, Ramtine Tofighi Shirazi
Category Software
Tags audit, OSTIF, software, vulnerability, 2025
The Open Source Technology Improvement Fund, Inc, thanks to funding provided by Sovereign Tech Fund, engaged with Quarkslab to perform a security audit of PHP-SRC, the interpreter of the PHP language.
Introduction
The Open Source Technology Improvement Fund, Inc, thanks to funding provided by Sovereign Tech Fund, engaged with Quarkslab to perform a security audit of PHP-SRC, the interpreter of the PHP language.
The audit aimed to assist PHP's core developers and the community in strengthening the project's security ahead of the upcoming PHP 8.4 release. The codebase was analyzed within a defined scope, which was established and agreed upon by both PHP's core developers and the OSTIF teams. Based on this scope and the allocated time frame for the audit, an attack model was developed and approved by the PHP team.
Scope
The assessment was conducted within a set timeframe, with the primary focus on identifying vulnerabilities and security issues in the code according to the defined attack model provided below.
The following scope of work was defined by PHP Foundation and the OSTIF.
-
Key tasks
- basic tooling evaluation;
- improve SAST tooling to enhance the existing GitHub CI without extra cost and with low maintenance;
- build fuzzers compatible with oss-fuzz for potential critical functions that are not currently covered;
- cryptographic and manual code review.
-
High priority tasks
- php-fpm master node and php-fpm worker glue code;
- FPM pool separation;
- MySQL Native Driver;
- RFC 1867 HTTP header parser and MIME handling;
- PDO: emulated prepares;
- JSON parsing with a focus on
json_decode; - OpenSSL external functions and its stream layer
ext/openssl; - libsodium integration
ext/sodium; - functionalities related to passwords
ext/standard/password.c; - functionalities related to hashing
ext/hash; - functionalities related to CSPRNG
ext/random/csprng.c.
-
Extra-considerations tasks: if applicable during the allocated time frame.
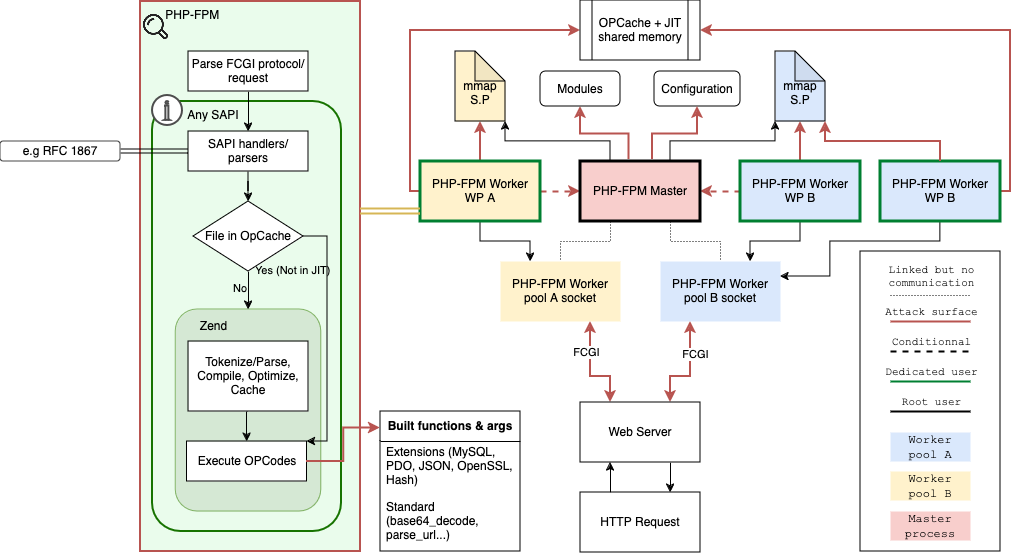
PHP-SRC attack surface, with respect to the provided scope-of-work, as defined by Quarkslab
Note: Quarkslab notes that the threat model and associated security issues scoring defined for this security assessment are different from PHP Foundation ones which can be found in their vulnerability disclosure policy.
To assess the security of PHP-SRC, Quarkslab's team first needed to familiarize themselves with the structure of the project and understand the key tasks outlined in the audit's scope. To achieve this, Quarkslab experts gathered and reviewed the available documentation and project resources. With a clear understanding of the features to be evaluated, Quarkslab developed an attack model that incorporated all the requested key tasks. This model was then presented to PHP's core developers, and once approved, the assessment began.
The evaluation employed a combination of dynamic and static analysis. The static analysis focused on scrutinizing the source code to identify vulnerabilities related to the implementation and logic of the specified assessment targets. Dynamic analysis was used to complement the static review by speeding up the process through fuzzing and validating or refuting the hypotheses generated during the static analysis.
Findings
During the time frame of the security audit, Quarkslab has discovered several security issues and vulnerabilities, among which:
- 2 security issues considered as high severity;
- 6 security issues considered as medium severity;
- 9 security issues considered as low severity;
- 10 issues considered informative.
Most vulnerabilities have been shared via security advisories on the PHP-SRC GitHub repository. Other bugs and issues are provided only in this report.
Four CVEs were issued, namely:
- CVE-2024-9026 for LOW-2;
- CVE-2024-8925 for LOW-4;
- CVE-2024-8928 for HIGH-1;
- CVE-2024-8929 for HIGH-2.
💡 Audit report
Complete details can be found in the audit report.Important:
This audit report contains two security issues currently redacted while PHP maintainers are actively working on the fixes. Details will be provided after fixes are applied by PHP maintainers. Fixes are complex and in progress.
| ID | Name | Perimeter |
|---|---|---|
| HIGH-1 | Details to be shared after fixes are applied (CVE-2024-8928). | - |
| HIGH-2 | Leak partial content of the heap through heap buffer over-read (CWE-122) - CVE-2024-8929 | MySQL driver |
| MED-1 | Denial of service of the PHP application and the CPU core used by the PHP-FPM worker instance which is loaded to its maximum capacity (CWE-833) | FPM |
| MED-2 | Details to be shared after fixes are applied. | - |
| MED-3 | Memory leak (CWE-401) | PDO |
| MED-4 | OpenSSL - short keys are padded (CWE-1240) | Cryptography |
| MED-5 | OpenSSL - the user’s IV is overwritten (CWE-1240) | Cryptography |
| MED-6 | OpenSSL - DH parameters not verified (CWE-1240) | Cryptography |
| LOW-1 | Bad supplied UID or GID for PHP-FPM worker pool can trigger an integer overflow and create confusion on actual used UID/GID, or may repeatedly crash the starting workers (CWE-190) | PHP-FPM configuration |
| LOW-2 | Logs from workers may be altered (CWE-1287, CWE-117) - CVE-2024-9026 | PHP-FPM |
| LOW-3 | Integer Overflow when parsing php.ini configuration values (CWE-190) |
Form-based File Upload (RFC 1867) |
| LOW-4 | Erroneous parsing of multipart form data (CWE-1286) - CVE-2024-8925 | Form-based File Upload (RFC 1867) |
| LOW-5 | Abnormal system resources consumption that could result in a crash (CWE-400) | MySQL driver |
| LOW-6 | OpenSSL - long keys are truncated (CWE-1240) | Cryptography |
| LOW-7 | OpenSSL - IVs are truncated or NUL-padded (CWE-1204) | Cryptography |
| LOW-8 | OpenSSL - CSR returned if signing failed (CWE-1059) | Cryptography |
| LOW-9 | OpenSSL - key_length not handled properly (CWE-320) |
Cryptography |
| INFO-1 | Accepted multipart request boundaries with invalid sizes (CWE-130) | Form-based File Upload (RFC 1867) |
| INFO-2 | Accepted invalid characters inside a boundary (CWE-1286) | Form-based File Upload (RFC 1867) |
| INFO-3 | Parsing of inherently invalid multipart requests (CWE-130) | Form-based File Upload (RFC 1867) |
| INFO-4 | Wrong boundary extraction from a non-standard request (CWE-241) | Form-based File Upload (RFC 1867) |
| INFO-5 | Logical buffer over-read (CWE-126) | MySQL driver |
| INFO-6 | OpenSSL - passphrase is not a good name (CWE-1099) | Cryptography |
| INFO-7 | OpenSSL - missing documentation of openssl_seal (CWE-1059) |
Cryptography |
| INFO-8 | OpenSSL - missing and erroneous documentation of openssl_csr_new (CWE-1059) |
Cryptography |
| INFO-9 | OpenSSL - missing ciphers (CWE-327) | Cryptography |
| INFO-10 | PBKDF2 - weak or absent recommendation (CWE-327) | Cryptography |
Conclusion
Quarkslab identified several vulnerabilities and bugs in PHP-SRC, many of which were found to pose significant risks in the context of PHP-FPM, where PHP scripts are executed continuously by the same OS process, making resource management crucial.
Quarkslab recognizes the considerable security efforts made by PHP's developers to safeguard the tool. Additionally, Quarkslab provided recommendations and strategies for addressing the vulnerabilities, helping to strengthen the open-source tool and enhance its security moving forward.
Finally, Quarkslab would like to thank the OSTIF team and the PHP Foundation and PHP-SRC maintainers for their support and collaboration throughout this security audit.