Authors Mihail Kirov, Sebastien Rolland
Category Software
Tags audit, OSTIF, software, Kubevirt, 2025
The Open Source Technology Improvement Fund, Inc., thanks to funding provided by Sovereign Tech Fund (STF), engaged with Quarkslab to perform a security audit of KubeVirt.
Introduction
Security is a core concern in the development of any open-source project. To ensure reliability and resilience, many teams choose to conduct independent audits that help identify potential weaknesses and strengthen their systems. In this context, Quarkslab experts recently performed a security assessment of KubeVirt with the goal of supporting its developers and community in improving the overall security of the ecosystem.
The audit provided valuable insights into potential vulnerabilities, assessed the alignment between the specification and its implementation, and offered concrete recommendations to enhance the project’s security posture.
The security evaluation followed a methodology that began with threat modeling, and combined static analysis, and dynamic testing. This approach enabled Quarkslab’s team to obtain an in-depth understanding of Kubevirt’s architecture, accurately define its attack surface, and identify potential vulnerabilities through both code-level inspection and runtime behavior analysis. Dynamic testing included targeted fuzzing campaigns. The report describes the steps of the vulnerability research we conducted.
Scope
The audit focused on the following components, which are responsible for the core virtualization functionality, and their interactions.
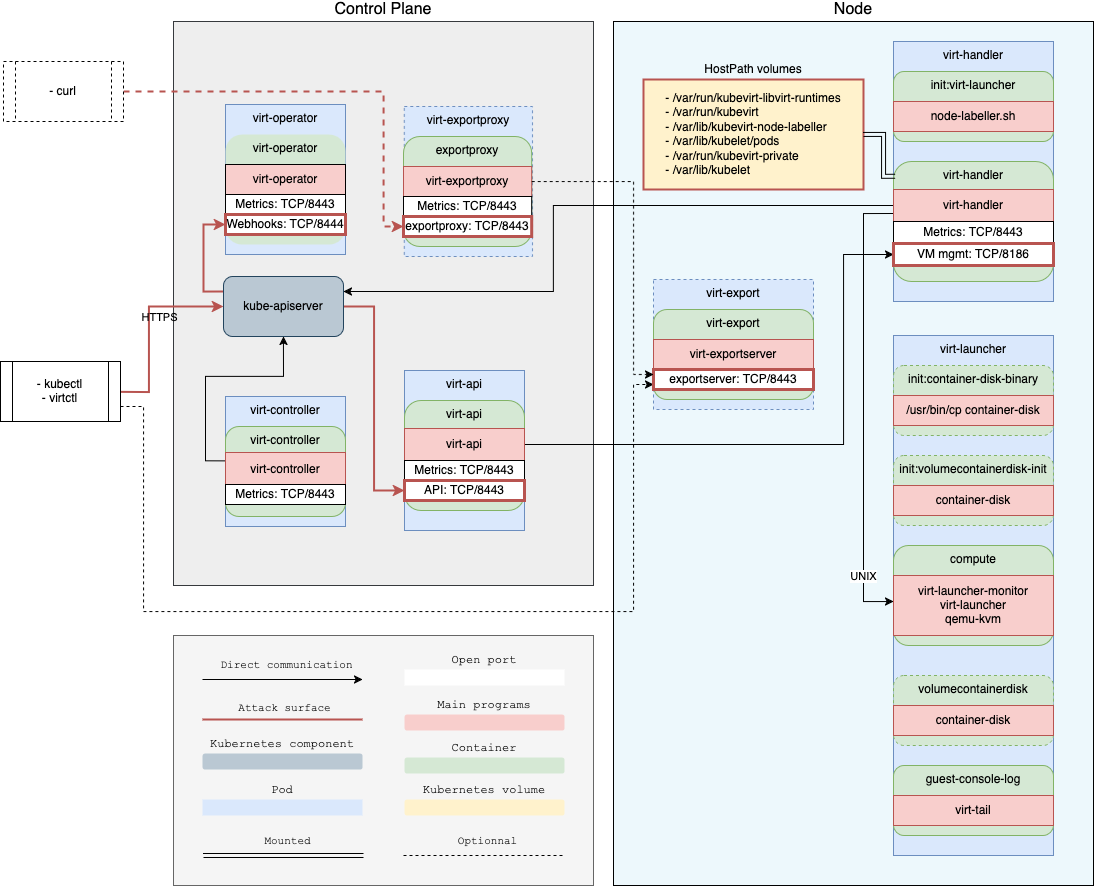
Findings
The table below summarizes the findings of the audit. A total of 15 vulnerabilities were identified: 1 of high severity, 7 of medium severity and 4 of low severity.
| ID | Title | Severity | Perimeter | CVE IDs |
|---|---|---|---|---|
| HIGH-6 | Arbitrary Host File Read and Write | High | virt-handler | CVE-2025-64324 |
| MED-2 | Authentication Bypass in Kubernetes Aggregation Layer | Medium | virt-api | CVE-2025-64432 |
| MED-3 | Improper TLS Certificate Management Handling Allows API Identity Spoofing | Medium | virt-handler | CVE-2025-64434 |
| MED-5 | Excessive Role Permissions Could Enable Unauthorized VMI Migrations Between Nodes | Medium | virt-handler | CVE-2025-64436 |
| MED-7 | Arbitrary Container File Read | Medium | virt handler-virt-launcher | CVE-2025-64433 |
| MED-8 | VMI Denial-of-Service (DoS) Using Pod Impersonation | Medium | virt-controler (VM) | CVE-2025-64435 |
| MED-9 | Isolation Detection Flaw Allows Arbitrary File Permission Changes | Medium | virt-handler, virt-launcher | CVE-2025-64437 |
| MED-12 | Privileged Operator Deployed Outside the Kubernetes Control Plane | Medium | virt-operator | / |
| LOW-4 | Lack of Common Name (CN) Verification in TLS Certificates | Low | virt-handler | / |
| LOW-13 | Webhook Server doesn’t Enforce Mutual Authentication and is Exposed to the Whole Cluster | Low | virt-operator | / |
| LOW-14 | Host devices exposed by KubeVirt are accessible clusterwide | Low | KubeVirt CR - virt-handler | / |
| LOW-15 | Sidecar Feature Gate May Allow Unauthorized Access to privileged components and Modification of VMI Configurations | Low | virt-launcher | / |
| INFO-1 | Crash Triggered by Unoptimized Build | Info | virt-handler | / |
| INFO-10 | Arbitrary Container File Mount Violating the Specification | Info | virt-handler | / |
| INFO-11 | Unhandled Exception Leads to a Crash | Info | virt-handler | / |
Note: At the time of writing, the identified vulnerabilities have been reported and received their respective CVE numbers.
Conclusion
Quarkslab identified several vulnerabilities and implementation bugs within KubeVirt. While most of these issues require specific preconditions or elevated privileges to be exploited, such as a compromised node or access to a KubeVirt component, their presence still highlights areas of potential risk in certain deployment scenarios.
Quarkslab acknowledges the significant security engineering efforts invested by the KubeVirt development team. The architecture demonstrates a strong emphasis on isolation, privilege boundaries, and container runtime hardening, which collectively raise the bar for successful exploitation.
We truly enjoyed collaborating with the OSTIF and would like to thank the Kubevirt teams for their openness, availability, and the constructive discussions that made this collaboration so effective.